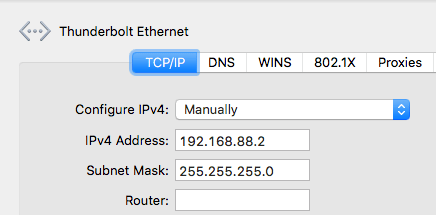
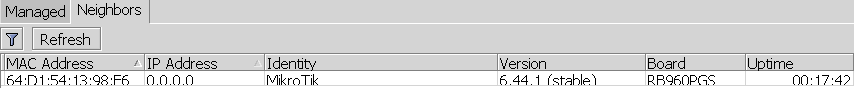
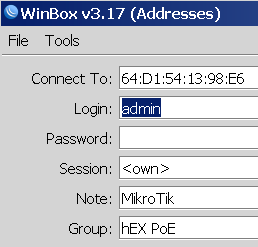
If you own a Mikrotik CCR device based on NAND memory, then be prepared that it will die.
I had this on a (now discontinued [WayBack] MikroTik Routers and Wireless – Products: CCR1009-8G-1S-1S+PC, superseded by the less functional [WayBack] MikroTik Routers and Wireless – Products: CCR1009-7G-1C-1S+PC, which is also NAND based).
Many more people had this or very similar problems:
- [WayBack] Corrupted routerboard firmware prevents booting – MikroTik
- [WayBack] CCR-1009-8G1S-1S Stuck at Starting Kernel – MikroTik
- [WayBack] ccr1009-8g-1s-1s+ stop in loading kernel from nand – MikroTik
- [WayBack] CCR-1016 ”loading kernel from nand ” Problem – MikroTik
- [WayBack] CCR Router Upgrades and often Fails with Reboot Loop – MikroTik
- [WayBack] CCR 1036-12G-EM reboot problem – MikroTik
- [WayBack] ccr 1009 after reboot/power loss boot loop – MikroTik
- [WayBack] CCR hangs on boot – MikroTik
- [WayBack] Mikrotik bricked by backup, reset button not working anymore – MikroTik
- [WayBack] Corrupted routerboard firmware prevents booting – MikroTik
- [WayBack] Cannot netinstall a CRS125 due to reboot loop – MikroTik
- [WayBack] RB493G, 60.0% Bad Blocks!!! What should I do now? – MikroTik
It also happens due to bad capacitors on the (also discontinued) [WayBack] MikroTik Routers and Wireless – Products: RB1200:
- [WayBack] RB1200 + Router keeps rebooting in loop (on power up one beep then it continues in loop) – MikroTik
There have been quite a few NAND related changes to the firmware over the years that have to do with handling corruption:
- [WayBack] mikrotik-tools/changelog-historic at master · 0ki/mikrotik-tools · GitHub from [WayBack] GitHub – 0ki/mikrotik-tools: Tools for Mikrotik devices
- [WayBack] www.mikrotik.ro/docs/changelog.txt
If you are really lucky (I was not), then it is a bad power supply: [WayBack] bootloop on CCR1036-12g-4s (almost 5 years old) [SOLVED] – MikroTik.
Sometimes you can partially recover using the Console port or NetInstall, but eventually you will trip another part of the faulty NAND storage and it will die again, until it has spent all its lives.
Unlike a cat, those are usually far less than 9 lives.
If you do need to recover, the links might help you:
- [WayBack] Recover a Broken Mikrotik Device | Murray’s Blog
- [WayBack] Manual:System/Serial Console – MikroTik Wiki
- [WayBack] Manual:Special Login – MikroTik Wiki
- [WayBack] Manual:RouterBOOT – MikroTik Wiki
- [WayBack] Manual:Netinstall – MikroTik Wiki
–jeroen