xkcd: Heartbleed Explanation, or why you should reset passwords, certificates and request new credit cards.
Posted by jpluimers on 2014/04/11
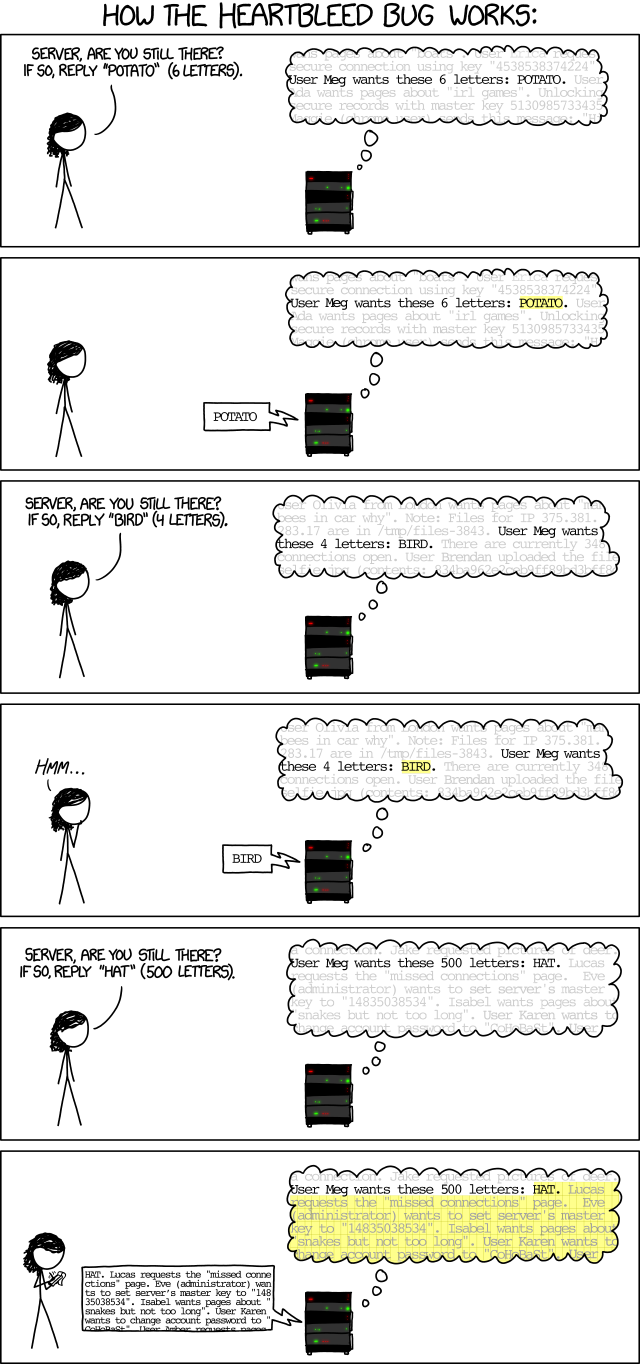
In layman’s terms/pictures: xkcd: Heartbleed Explanation.
If you still don’t get it: anyone with any HTTPS connection to a once vulnerable system could copy data out of that system. There is no guarantee that data did not contain your identity (username, password, public key, credit card check-digits, etc) or server identity (private and public key).
Since often you cannot prove a system was using OpenSSL, there is no way to prove your data didn’t get copied.
–jeroen (who just discovered this is post #2000 on my blog; ain’t this cool? <g>)






More OpenSSL and certificate things (in the aftermath of Heartbleed) « The Wiert Corner – irregular stream of stuff said
[…] jpluimers on xkcd: Heartbleed Explanation,… […]
IL said
Does heartbleed attack extend to secured POP3S/IMAPS/SMTPS TLS or STARTTLS connections?
jpluimers said
From what I read it happens for all TLS connections that support heartbeat.
IL said
It does! http://heartbleed.com/
How widespread is this?
Most notable software using OpenSSL are the open source web servers like Apache and nginx. The combined market share of just those two out of the active sites on the Internet was over 66% according to Netcraft’s April 2014 Web Server Survey. Furthermore OpenSSL is used to protect for example email servers (*SMTP, POP and IMAP* protocols), chat servers (*XMPP* protocol), virtual private networks (*SSL VPNs*), network appliances and wide variety of client side software. Fortunately many large consumer sites are saved by their conservative choice of SSL/TLS termination equipment and software. Ironically smaller and more progressive services or those who have upgraded to latest and best encryption will be affected most. Furthermore OpenSSL is very popular in client software and somewhat popular in networked appliances which have most inertia in getting updates.
jpluimers said
On the positive side: OpenSSL 0.9.8 used by many servers doesn’t suffer from this (there is no TLS heartbeat support in it).
IL said
Yep and thankfully, Microsoft IIS does not contain this bug.
jpluimers said
IIS has different bugs (;
marco wobben said
serious ouch indeed!