XZ 5.6.x are backdoored and present in many systems: downgrade to 5.4.x or earlier now; consider libarchive compromised until proven otherwise
Posted by jpluimers on 2024/03/30
Edit 20240331: because of
https://mastodon.social/@kobold/112183756981119562
Debian is working on reverting back to even earlier than 5.4.x
[Wayback/Archive] #1068024 – revert to version that does not contain changes by bad actor – Debian Bug report logs
> I'd suggest reverting to 5.3.1. Bearing in mind that there were security> fixes after that point for ZDI-CAN-16587 that would need to be reapplied.
Note that reverted to such an old version will break packages that usenew symbols introduced since then. From a quick look, this is at least:- dpkg- erofs-utils- kmod
Having dpkg in that list means that such downgrade has to be plannedcarefully.
Original post:
Everything I know about the XZ backdoor
- [Wayback/Archive] Everything I know about the XZ backdoor
- [Wayback/Archive] blog.holz.nu/2024/03/29/0.html: xz wurde gebackdoort
- [Wayback/Archive] xz-utils backdoor situation · GitHub
Note that because of the Wayback Machine limit of 5 archivals per URL per day, the archived versions are rapidly getting out-of-date.
It is way worse:
[Wayback/Archive] Thread by @_ruby on Thread Reader App – Thread Reader App
@_ruby: The setup behind the CVE-2024-3094 supply-chain attack is fascinating. I originally wanted to finish and share a tool to audit other OSS projects for anomalous contributor behavior, but I feel what I found tr……
How it was found:
Analogy on how it was found:
Via:
Related:
If you are running homebrew on a Mac, then update too:
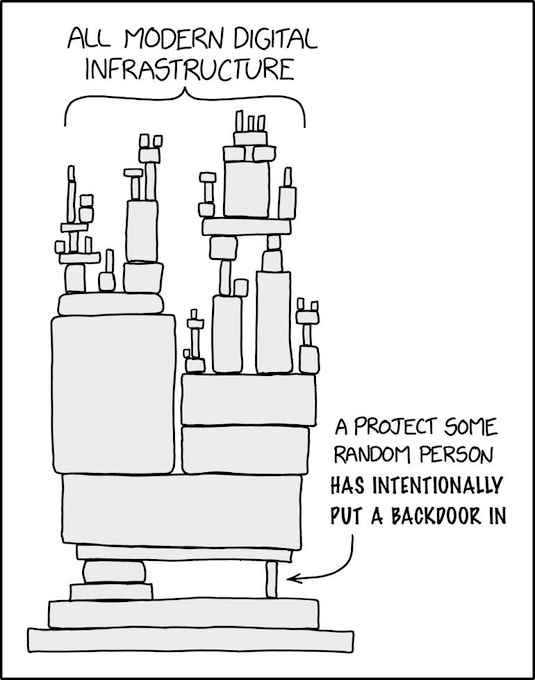
Of course this “XKCD dependency” adoption applies:






Leave a comment