[WayBack] Kristian Köhntopp – Google+:
The S in IoT is for Security, and the U is for Update Policy.
Posted by jpluimers on 2017/10/18
[WayBack] Kristian Köhntopp – Google+:
The S in IoT is for Security, and the U is for Update Policy.
Posted in Development, Fun, Power User, Quotes, Software Development, WiFi | Leave a Comment »
Posted by jpluimers on 2017/10/18
On the long-read list: [WayBack] The Software Development Process – Science, Engineering, Art, or Craft? – CodeProject
Posted in Agile, Development, Software Development | Leave a Comment »
Posted by jpluimers on 2017/10/18
One day this will be extremely useful to me: [WayBack] GitHub – sinbad/spriterecolour: Sprite processor to allow dynamic recolouring
Via: [WayBack] SpriteRecolour, an open source sprite recolouring tool · SteveStreeting.com
TL;DR:
- SpriteRecolour project page
- Download binaries (Mac, Win x86/x64, Linux x86/x64)
- SpriteRecolour example project in Unity
Posted in Algorithms, Development, Software Development | Leave a Comment »
Posted by jpluimers on 2017/10/17
[WayBack] Google’s AI can create better machine-learning code than the researchers who made it:
Google’s AutoML project has yielded significant advances in the ability for machine-learning systems to replicate and improve AI code.
Via:
–jeroen
Posted in AI and ML; Artificial Intelligence & Machine Learning, Development, LifeHacker, Power User, science, Software Development | Leave a Comment »
Posted by jpluimers on 2017/10/17
People love @TMSSoftwareNews because of the short bug-fix turnaround. In this case 2.5 hours: [WayBack] @jpluimers: @TMSsoftwareNews when entering a perfectly valid email address like word.word+tag.subtag@gmail.com: Please enter a valid Email Address.
–jeroen
Posted in Delphi, Development, Software Development | Leave a Comment »
Posted by jpluimers on 2017/10/17
I ordered a UPS PIco HV3.0 A Stack 450 Plus and it arrived without any documentation on how to solder the parts together.
So I tried searching for them: https://www.google.com/search?q=UPS+PIco+HV3.0+A+Stack+450+Plus+installation+instructions which turned mostly github based URLs.
I learned there is a bit on github:
But despite code and documentation being there, no installation instructions on how to solder the stuff together.
Luckily, they responded quickly to my tweet So I got my “UPS PIco HV3.0 A Stack 450 Plus” @ModMyPi but no assembly instructions. Where do all the non-soldered parts go when using RPi3? and a quick respons thread revealing I needed 03_0x38_W_UPS PIco HV3.0.pdf which – TADAAAA – is on Google drive and on the forums at [WayBack] UPS PIco Firmware Update & Troubleshooting : Technical Support
So despite github providing an excellent platform for discussion and storing documentation, something archaic like a forum is used to store data in a disorganised way.
Too bad, as the document itself is 100+ page of invaluable documentation.
So in case of future bit-rot, here are the links:
Posted in Development, Hardware Development, Hardware Interfacing, Raspberry Pi | Leave a Comment »
Posted by jpluimers on 2017/10/17
[WayBack] TMS Software | Blog | TEncryptedIniFile: easy to use class for handling app settings with encryption
via: [WayBack] A new blog has been posted:TEncryptedIniFile: easy to use class for handling app settings with encryption – Michael Thuma – Google+
I wonder how that works with encryption algorithms based on thin Delphi wrappers around proven open source encryption libraries.
–jeroen
PS: Note the G+ link died. Not sure why, but that’s why I archived the original as a WayBack link when writing this post.
Posted in Delphi, Development, Software Development | 4 Comments »
Posted by jpluimers on 2017/10/16
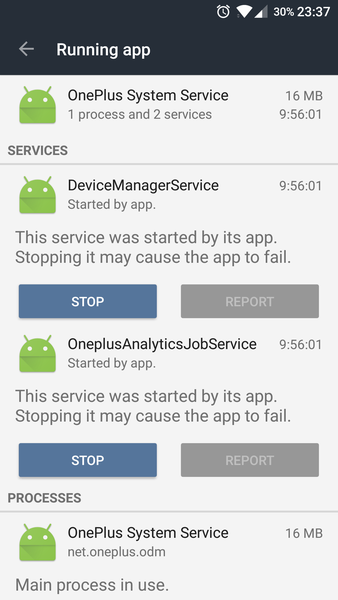 Remove the OnePlus Analytics service because of privacy violations:
Remove the OnePlus Analytics service because of privacy violations:
Source: [WayBack] OnePlus OxygenOS built-in analytics
We take a look at the analytics built into the OxygenOS, the flavour of Android built by phone manufacturer OnePlus.
The analytics data is sent over https, but it contains way too much information on your privacy.
This also taught me about this interesting project: [WayBack] OWASP Zed Attack Proxy Project – OWASP
These tweets describe how to disabled it:
pm uninstall -k --user 0 pkg“pm list packages | grep oneplus‘It was also present OnePlus Five, I found it through:
Until removed, it restarts at every boot.
Removing the service seems more permanent than the alternative [WayBack] Dear OnePlus, please stop spying on my phone:
offIt is unclear to me what turned that option on in the first place.
–jeroen
via: [WayBack] Welp. As a OnePlus owner, this makes me pretty damn unhappy :/ https://www.chrisdcmoore.co.uk/post/oneplus-analytics/ +Colm Buckley – Kristian Köhntopp – Google+
Posted in Android Devices, OnePlus Five, OnePlus Two, Power User, Privacy | Leave a Comment »
Posted by jpluimers on 2017/10/16
I noticed that on my Mac, Beyond Compare wasn’t able to edit diffed files when it had been started from SourceTree. This struck me as odd since on Windows this worked fine. So I did a bit of digging and found out both SourceTee and I screwed up:
Luckily [WayBack] Zoë Peterson (lead developer on Beyond Compare and formerly Turbo Power Abbrevia project admin) had answered this before, and all these show “Editing disabled” in the user-interface:
Beyond Compare will disable editing of a file any of the following reasons:
- It’s one of the input files in a 3-way merge
- The comparison was cancelled
- The comparison encountered an error (corrupt file, invalid character encoding, out of memory, gamma rays, etc)
- The file format’s conversion settings don’t support converting back to the original format (MS Word, PDF)
- The file is on a read-only “filesystem” (7zip/RAR/CHM archives, CD/DVD-ROMs)
- A file or parent folder had editing explicitly disabled by the user in the session settings or using the
/rocommand line switches- The viewer itself doesn’t support editing (eg, Hex Compare)
Source: [WayBack] version control – Beyond Compare 3 editing disabled – Stack Overflow
So the last instruction should be:
Set both
Visual Diff ToolandMerge TooltoOther, then set both theDiff CommandandMerge Commandto the value you obtained above (in my case/usr/local/bin/bcomp) and these arguments:
Diff Command Arguments
"$LOCAL" "$REMOTE"Merge Command Arguments
"$LOCAL" "$REMOTE" "$BASE" "$MERGED"
Note that somewhere during 2.2, SourceTree has added Beyond Compare integration and fixed some of the issues, but there are still issues left:
There is only one occasion where the UI does not show “Editing Disabled”, but where you cannot edit the file itself (you can only edit the current line in the line diff view at the bottom of the UI). Zoë mentioned that too:
…
Also, the Full Edit (F2) toggle in the Text Compare View menu switches between inline editing and line-based mode. If it’s disabled you can copy/delete whole lines and type in the line details edits at the bottom of the window, but the main windows won’t have a cursor, typing is disabled, and it will always select whole lines. Unlike the above items, this doesn’t show “Editing Disabled” in the status bar.
Source: [WayBack] version control – Beyond Compare 3 editing disabled – Stack Overflow
By default this setting is bound to the F2 key on Windows, so if you accidentally press that when Beyond Compare is active, you might be in for a surprise.
Screen shots:
Posted in Beyond Compare, Encoding, Power User | Leave a Comment »
Posted by jpluimers on 2017/10/16
All of our house is wired by ethernet for a reason…
WPA2 Flawed. Once again, it turns out that designing something properly secure is really, really, REALLY hard.
[WayBack] Severe flaw in WPA2 protocol leaves Wi-Fi traffic open to eavesdropping https://arstechnica.com/… – Lars Fosdal – Google+
[Archive.is] If fixes exist, third party firmware will have it in days. Most OEMs, never. I do worry a lot about unfixable flaws in the wifi standards… – Kristian Köhntopp – Google+:
Dave reminds us that there is a reason why people mod the firmware of their Wifi routers, and that reason is actually now more critical than ever.
Via [WayBack] https://www.krackattacks.com/ has a FAQ. Some interesting questions from there:… – Kristian Köhntopp – Google+:
[WayBack] KRACK Attacks: Breaking WPA2 : This website presents the Key Reinstallation Attack (KRACK). It breaks the WPA2 protocol by forcing nonce reuse in encryption algorithms used by Wi-Fi.
Since we’re talking security, watch your RSA as it is way worse than the WPA2 one: [Archive.is]
[WayBack] Dan Goodin @dangoodin001: 2nd major crypto vulnerability being disclosed Monday involves millions of 1024- and 2048-bit RSA keys that are practically factorizable.
[WayBack] ROCA: Vulnerable RSA generation (CVE-2017-15361) [CRoCS wiki]
The time complexity and cost for the selected key lengths (Intel E5-2650 v3@3GHz Q2/2014):
[WayBack] New vulnerabilities found in RSA 1024 and 2048 bit keys. Estimated cost of cracking based on access to the Public key only: 1024 bit: $40 2048 bit: $20k… – Lars Fosdal – Google+
Jan Wildeboer did a nice explanation in laymen terms of both security issues published today:
–jeroen
Posted in LifeHacker, Power User, Security, WiFi | Leave a Comment »