Archive for the ‘*nix’ Category
Posted by jpluimers on 2019/04/22
I wondered [WayBack] linux – Why is this a binary multi-megabyte blob /etc/udev/hwdb.bin under /etc? – Unix & Linux Stack Exchange.
All my OpenSuSE systems had the /etc/udev/hwdb.bin file with sizes varying between 7.5 and 10 megabytes with many of the zypper dist-upgrade causing updates.
Luckily the system also contains these files which had valid unit definitions, so the file was generated/updated during boot:
/usr/bin/systemd-hwdb/usr/lib/systemd/system/sysinit.target.wants/systemd-hwdb-update.service/usr/lib/systemd/system/systemd-hwdb-update.service
Thanks [WayBack] nwildner for answering that question!
So after installing etckeeper and performing etckeeper init you can immediately remove it from the git repository:
# cd /etc
# git rm --cached /etc/udev/hwdb.bin
rm 'udev/hwdb.bin'
# git commit -m "no need for /etc/udev/hwdb.bin to be under revision control as systemd-hwdb maintains it"
For more background, see [WayBack] How to make Git “forget” about a file that was tracked but is now in .gitignore? – Stack Overflow.
–jeroen
Posted in *nix, *nix-tools, etckeeper, Linux, openSuSE, Power User, SuSE Linux, systemd, Tumbleweed | Leave a Comment »
Posted by jpluimers on 2019/04/19
Still learning postfix configuration, below are some links on how to enable various blacklists that use the RBL DNS (aka [WayBack] DNSBL) way of operations.
They are centered around using the of the [WayBack] Postfix Documentation entry reject_rbl_client listings:
Basically reject_rbl_client is part of smtpd_client_restrictions.
TODO:
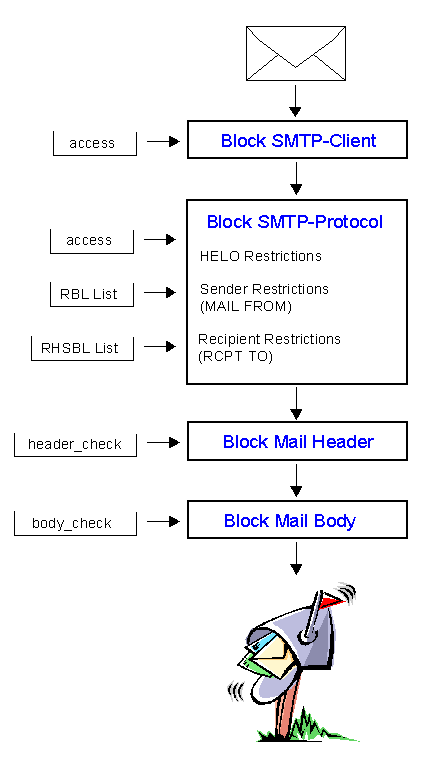 I need to dig further into some other blacklist options than
I need to dig further into some other blacklist options than reject_rbl_client: reject_rhsbl_client, reject_rhsbl_reverse_client, reject_rhsbl_sender or reject_rhsbl_recipient restriction.
Then I need to go through these links:
Some blacklist checking links:
- [WayBack] DNSBL Information – Spam Database and Blacklist Check
- [WayBack] IP Address Blacklist Check
- [WayBack] The Spamhaus Project – ZENzen.spamhaus.org should be the only spamhaus.org DNSBL in your IP blocklist configuration. You should not use ZEN together with other Spamhaus IP blocklists, or with blocklists already included in our zones (such as the CBL) or you will simply be wasting DNS queries and slowing your mail queue.
Caution: Because ZEN includes the XBL and PBL lists, do not use ZEN on smarthosts or SMTP AUTH outbound servers for your own customers (or you risk blocking your own customers). Do not use ZEN in filters that do any ‘deep parsing’ of Received headers, or for anything other than checking IP addresses that hand off to your mailservers.
–jeroen
Posted in *nix, *nix-tools, postfix, Power User | Leave a Comment »
Posted by jpluimers on 2019/04/15
Cool tool if you use Postfix: mail-filters/Makefile at master · fumiyas/mail-filters.
You set it up like this:
cd /etc/postfix
wget https://raw.githubusercontent.com/fumiyas/mail-filters/master/postfix/Makefile
Then each time you change your postfix configuration:
cd /etc/postfix
make
In that directory, it will (re)generate a Makefile.postmapbased on the lines with hash in main.cf, then make each .db file from the source hash file.
After that you have to manually restart postfix, which depends on your Linux flavour.
Similar solutions:
–jeroen
Posted in *nix, *nix-tools, Development, Makefile, postfix, Power User, Scripting, Software Development | Leave a Comment »
Posted by jpluimers on 2019/04/15
Just when I thought I made a note of a password I hardly ever use, I didn’t, luckily this open source tools understands how to recover many kinds of passwords: AlessandroZ/LaZagne: Credentials recovery project.
–jeroen
Posted in *nix, *nix-tools, Chrome, Development, DVCS - Distributed Version Control, Firefox, git, Internet Explorer, Office, Opera, Outlook, Power User, Python, Scripting, Skype, Software Development, Source Code Management, Web Browsers, WiFi, Windows | Leave a Comment »
Posted by jpluimers on 2019/04/15
If you see the below in your Postfix log when trying to test your config, then the SASL configuration is empty. Oddly that seems the default on OpenSuSE for a while now, despite it providing cyrus SASL out of the box.
Sep 15 14:30:07 katrien postfix/smtpd[12719]: fatal: bad string length 0 < 1: smtpd_sasl_path =
Sep 15 14:30:08 katrien postfix/master[12400]: warning: process /usr/lib/postfix/smtpd pid 12719 exit status 1
Sep 15 14:30:08 katrien postfix/master[12400]: warning: /usr/lib/postfix/smtpd: bad command startup -- throttling
Prior OpenSuSE versions had this in /etc/postfix/main.cf:
# SASL stuff
############################################################
smtp_sasl_auth_enable = no
smtp_sasl_security_options =
smtp_sasl_password_maps =
smtpd_sasl_auth_enable = no
#smtpd_sasl_path = private/auth
#smtpd_sasl_type = dovecot
Newer OpenSuSE versions have this:
# SASL stuff
############################################################
smtp_sasl_auth_enable = no
smtp_sasl_security_options =
smtp_sasl_password_maps =
smtpd_sasl_auth_enable = no
# cyrus : smtpd_sasl_type = cyrus, smtpd_sasl_path = smtpd
# dovecot : smtpd_sasl_type = dovecot, smtpd_sasl_path = private/auth
smtpd_sasl_path =
smtpd_sasl_type =
Despite the newer having these installed:
# rpm -qa | grep cyrus
cyrus-sasl-crammd5-2.1.26-14.2.aarch64
cyrus-sasl-2.1.26-14.2.aarch64
cyrus-sasl-plain-2.1.26-14.2.aarch64
cyrus-sasl-digestmd5-2.1.26-14.2.aarch64
cyrus-sasl-gssapi-2.1.26-14.2.aarch64
Solution:
smtpd_sasl_path = smtpd
smtpd_sasl_type = cyrus
Since the values for both lines are default, you could even comment them out; see the documentation:
–jeroen
Via: [WayBack] postfix IRC logs [July 26 – 2007]
Posted in *nix, *nix-tools, Linux, openSuSE, postfix, Power User, SuSE Linux, Tumbleweed | Leave a Comment »
Posted by jpluimers on 2019/04/12
Every now and then I hear about providers that refuse to hand over the VoIP SIP credentials.
If you do have access to your modem, you can Wireshark the WAN side, then reset the modem and capture traffic until it has obtained the VoIP information:
[WayBack] Telfort SIP (getest met Glasvezel) | Het leven van Teus & Simone:
Veel mensen op het forum van Telfort vragen zich af of ze de SIP gegevens kunnen krijgen voor telefonie zodat men de ExperiaBox niet hoeven te gebruiken. Gezien dat de Telfort Support deze gegevens…
Via:
–jeroen
Posted in *nix, *nix-tools, Internet, Power User, Wireshark | Leave a Comment »
Posted by jpluimers on 2019/04/12
Confused by crontab expressions? Me too, so I was happy to find: At minute 3 past every 12th hour: crontab.guru – the cron schedule expression editor.
It has a [WayBack] truckload of common crontab expressions, but more importantly allows you to live edit one, then explains in human terms what it means and when the schedule runs next.
If you like a step by step cron configurator, then you can try [WayBack] Cron Job Generator by GenerateIt.net but need to note it cannot interpret a cron expression.
–jeroen
Posted in *nix, *nix-tools, cron, Linux, Power User | Leave a Comment »
Posted by jpluimers on 2019/03/29
When connecting from my Mac to my ESXi rig, some commands (especially less) show this output:
WARNING: terminal is not fully functional
So I created this alias to connect from my Mac to the internal address of my ESXi rig:
alias ssh-esxi-X10SRH-CF-internal='TERM=xterm ssh -p 22 root@192.168.71.91'
The trick is the bold part: TERM=xterm (which you can also replace by export TERM=xterm; if you want future ssh sessions to use the same [wayback] TERM setting).
The reason is that the Mac defines the TERM variable as containing xterm-256 which is defined on the Mac itself, but ESXi has a hard time coping with it.
Some Mac OS and Xcode combinations had a problem with xterm-256 not being present ([WayBack] macos – Terminal strangeness after installing Xcode on Lion – Super User), but this isn’t the case on my system:
$ ls -alh `find /usr/share/terminfo | grep 'xterm-256color'`
-rw-r--r-- 1 root wheel 3.2K Jul 30 2016 /usr/share/terminfo/78/xterm-256color
On the Mac you really want to use xterm-256color as it looks way better than xterm-color or xterm: [WayBack] linux – What is the difference between xterm-color & xterm-256color? – Stack Overflow (thanks [WayBack] Chris Page!)
It seems I already did something similar on ESXi itself to get esxtop working: ESXi: when esxtop shows garbage. That was on the ESXi side and works as well for this problem too.
However, it is a bit harder to have a script run during ESXi boot time that sets this, so it is easier to fix this on the Mac side.
It works for all OS X and ESXi versions I’ve tested so far.
–jeroen
Posted in *nix, Apple, ESXi5.1, ESXi5.5, ESXi6, ESXi6.5, iMac, Mac, Mac OS X / OS X / MacOS, Mac OS X 10.4 Tiger, Mac OS X 10.5 Leopard, Mac OS X 10.6 Snow Leopard, Mac OS X 10.7 Lion, MacBook, MacBook Retina, MacBook-Air, MacBook-Pro, MacMini, macOS 10.12 Sierra, OS X 10.10 Yosemite, OS X 10.11 El Capitan, OS X 10.8 Mountain Lion, OS X 10.9 Mavericks, Power User, Virtualization, VMware, VMware ESXi | Leave a Comment »
Posted by jpluimers on 2019/03/11
Most tips are OK, but:
- for password related policies, please read these:
- If you do DNS, implement DNSSEC
- I think ipv6 is OK, but like ipv4 needs to be firewalled
- Be really careful with fail2ban and similar tools: they are easy ways to lock yourself out as well, for instance by someone doing a nice (D)DoS on you.
Tips: [WayBack] 40 Linux Server Hardening Security Tips [2017 edition] – nixCraft
Via:
–jeroen
Posted in *nix, *nix-tools, Encryption, Let's Encrypt (letsencrypt/certbot), Power User, Security | Leave a Comment »
Posted by jpluimers on 2019/03/08
TL;DR:
sudo -i is not an interactive logon to rootsudo -i bash is interactive and *does* execute /root/.bashrc
Source: [WayBack] sudo command doesn’t source /root/.bashrc – Unix & Linux Stack Exchange
–jeroen
Posted in *nix, *nix-tools, bash, Power User | Leave a Comment »








